Cybersecurity Incident Report Template
Cybersecurity Incident Report Template - Use this form to report any cybersecurity issues, breaches, hacks, malware, or any other incidents involving a 3rd party. Download lumiform’s free cyber security incident report template today and implement a robust strategy for managing cyber security incidents. Customize and download this cybersecurity incident report. Report and document cybersecurity incidents easily with our cybersecurity incident report form template. Analyze the incident to learn lessons and strengthen future response capabilities and resilience. Jane smith, it security analyst date and time of. Writing an effective cybersecurity incident report is a critical step in incident response. Incident response investigations require efficient and quick coordination. Date and time of incident: Formspal offers a free cybersecurity incident response report template. This report provides a detailed. Download lumiform’s free cyber security incident report template today and implement a robust strategy for managing cyber security incidents. Formspal offers a free cybersecurity incident response report template. When a cyber security incident occurs, timely and thorough action to manage the impact of the incident is a critical to an effective response process. Cybersecurity incident report is in editable, printable format. Download this cyber security incident report template design in word, google docs, pdf, publisher, indesign format. This template guides you through all the critical stages of incident response,. A unique identifier for the incident. The response should limit the potential. Jane smith, it security analyst date and time of. January 13, 2025, 3:15 pm reported by: The breach involved unauthorized access to sensitive customer data at [your. Enhance security with our detailed incident report templates. Stay prepared and handle cybersecurity incidents effectively with our comprehensive incident report template. Download this cyber security incident report template design in word, google docs, pdf, publisher, indesign format. Instead, consistent and transparent communication can mitigate losses, preserve reputation and maintain customer loyalty. Report and document cybersecurity incidents easily with our cybersecurity incident report form template. Our cybersecurity incident report template documents a cybersecurity incident within an organization, covering its classification, description, impact assessment, and. Incident response investigations require efficient and quick coordination. How was the incident detected /. Cybersecurity incident report is in editable, printable format. Use this form to report any cybersecurity issues, breaches, hacks, malware, or any other incidents involving a 3rd party. Formspal offers a free cybersecurity incident response report template. Tailored for quick, accurate documentation. Key components of an incident response playbook. This is why every company should include a cyber. Tailored for quick, accurate documentation. Incident response investigations require efficient and quick coordination. This form is designed for reporting cybersecurity incidents. The cyber risk assessment powerpoint template is a visually structured tool designed to help businesses, it teams, and security professionals analyze and present cyber threats. These playbooks provide fceb agencies with a standard set of procedures to identify, coordinate, remediate, recover, and track successful mitigations from incidents and. Date and time of incident: Writing an effective cybersecurity incident report is a critical step in incident response. January 13, 2025, 3:15 pm reported by: This form is designed for reporting cybersecurity incidents. Cybersecurity incident report is in editable, printable format. Get a free and fillable cybersecurity incident report template. This report outlines the details of a cybersecurity incident that occurred on october 15, 2023. Key components of an incident response playbook. This report provides a detailed. Xyz tech solutions recently faced a cybersecurity incident on february 12, 2025, involving a phishing attack targeting employee email accounts. A unique identifier for the incident. How was the incident detected / discovered?. Download an incident response template designed to strengthen the way security teams collect, document, and. Instead, consistent and transparent communication can mitigate losses, preserve reputation and maintain. A unique identifier for the incident. This is why every company should include a cyber. This report outlines the details of a cybersecurity incident that occurred on october 15, 2023. Enhance security with our detailed incident report templates. Instead, consistent and transparent communication can mitigate losses, preserve reputation and maintain customer loyalty. How was the incident detected / discovered?. Key components of an incident response playbook. Report and document cybersecurity incidents easily with our cybersecurity incident report form template. Incident response investigations require efficient and quick coordination. This form is designed for reporting cybersecurity incidents. Download this cyber security incident report template design in word, google docs, pdf, publisher, indesign format. Cybersecurity incident report is in editable, printable format. This report outlines the details of a cybersecurity incident that occurred on october 15, 2023. Download an incident response template designed to strengthen the way security teams collect, document, and. Download lumiform’s free cyber security incident. When a cyber security incident occurs, timely and thorough action to manage the impact of the incident is a critical to an effective response process. This template guides you through all the critical stages of incident response,. This report provides a detailed. Key components of an incident response playbook. Enhance this design & content with free ai. Get a free and fillable cybersecurity incident report template. Stay prepared and handle cybersecurity incidents effectively with our comprehensive incident report template. This report outlines the details of a cybersecurity incident that occurred on october 15, 2023. Editable and easy to download. Date and time of incident: Report and document cybersecurity incidents easily with our cybersecurity incident report form template. The cyber risk assessment powerpoint template is a visually structured tool designed to help businesses, it teams, and security professionals analyze and present cyber threats. Analyze the incident to learn lessons and strengthen future response capabilities and resilience. These playbooks provide fceb agencies with a standard set of procedures to identify, coordinate, remediate, recover, and track successful mitigations from incidents and. Download lumiform’s free cyber security incident report template today and implement a robust strategy for managing cyber security incidents. Use this form to report any cybersecurity issues, breaches, hacks, malware, or any other incidents involving a 3rd party.Cybersecurity Incident Report Template
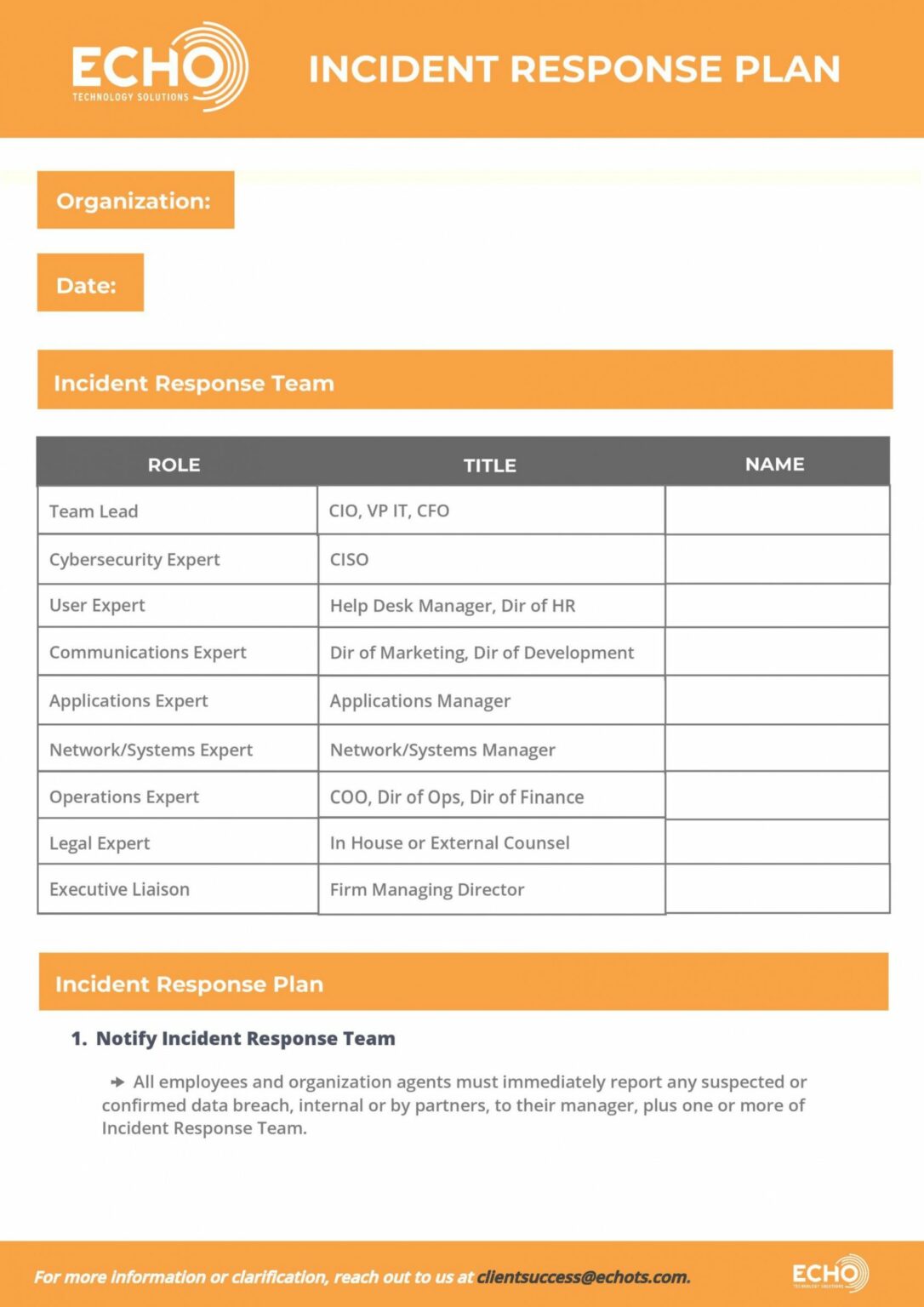
Incident cyber response template plan structure planning immediately
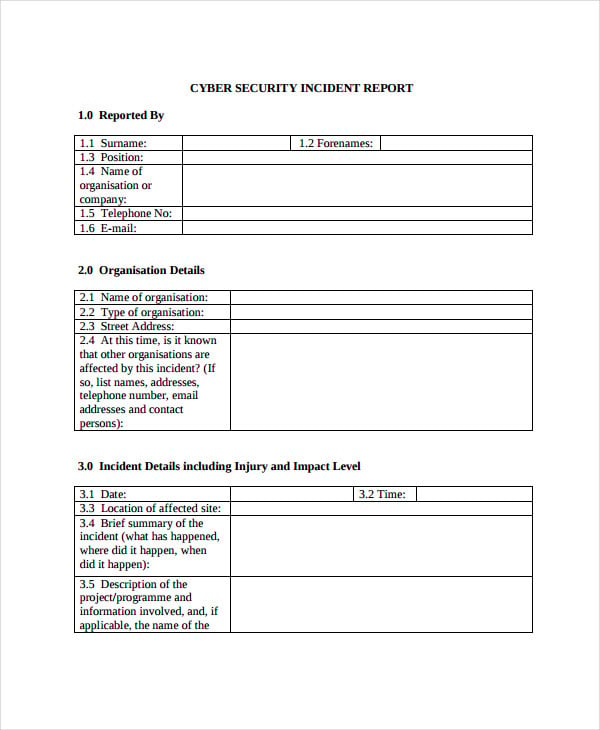
Cyber Security Incident Report Template Word
Free Security Incident Report Template Download in Word, Google Docs
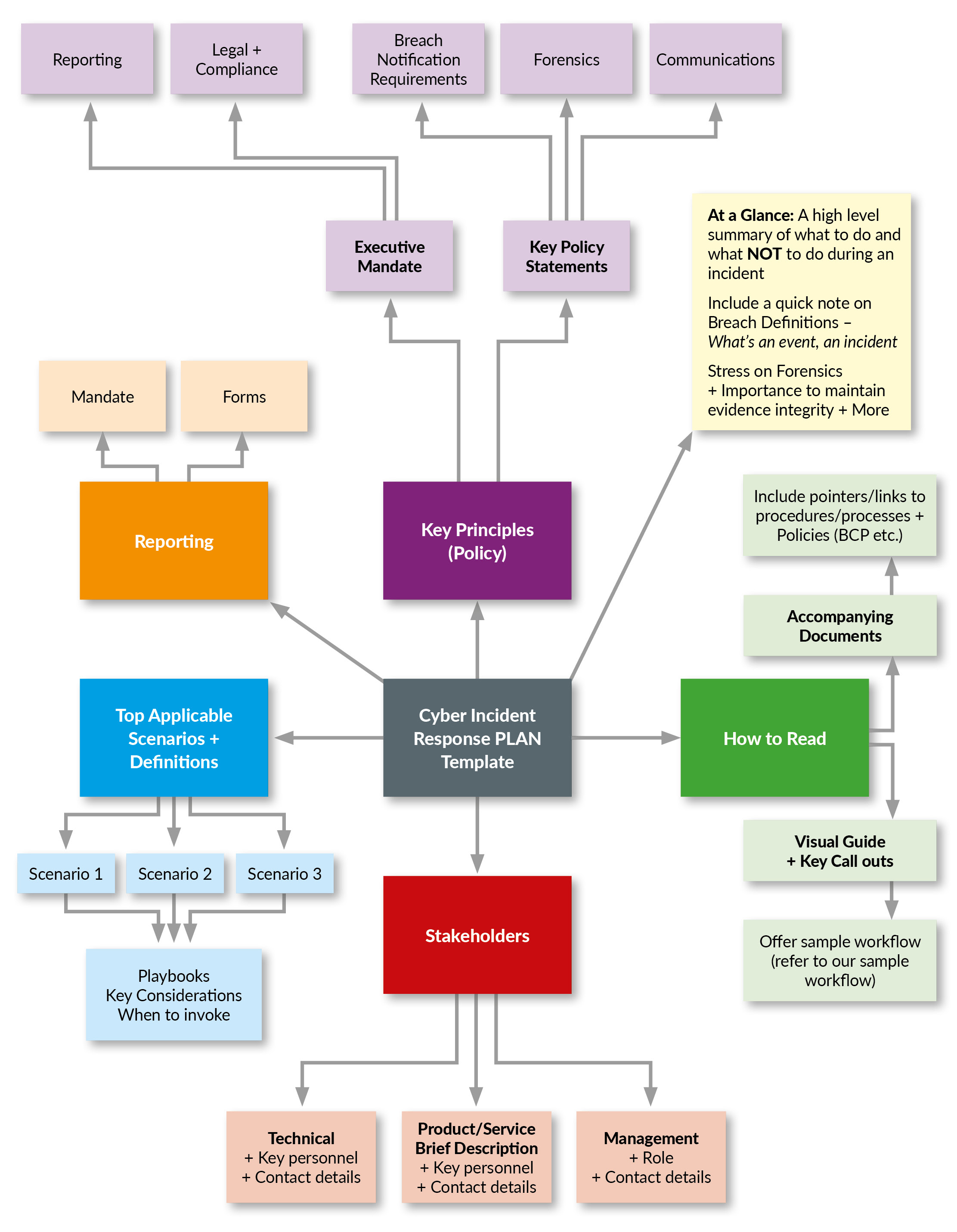
Free Cybersecurity Incident Response Plan Template Develop Your Plan
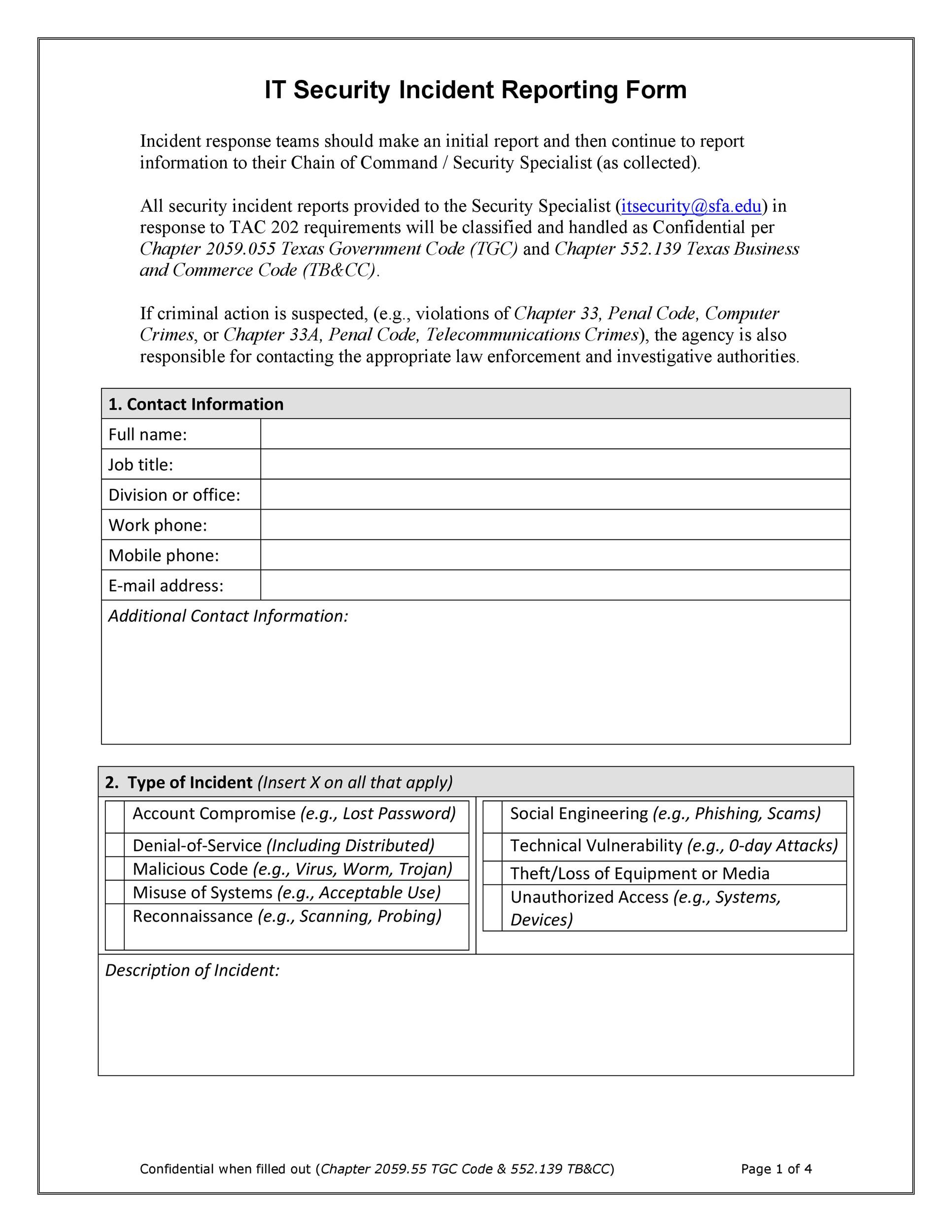
Cyber Security Incident Report Template in Word, PDF, Google Docs
Best Free Computer Incident Response Templates and Scenarios
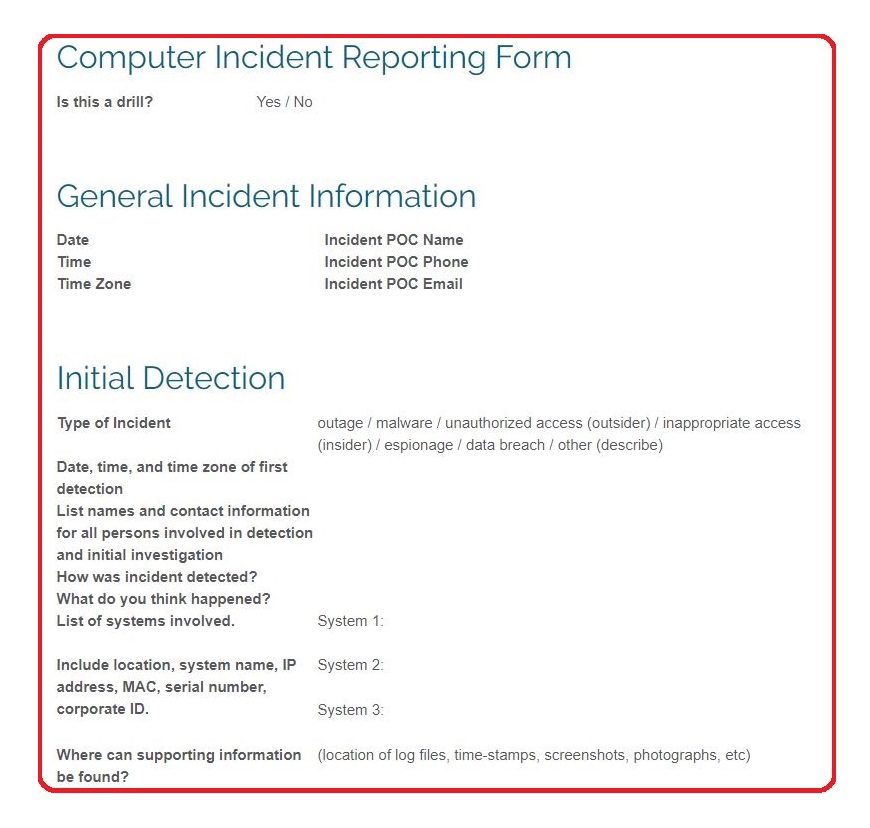
Free Cybersecurity (IT) Incident Report Template PDF Word eForms
Cybersecurity Incident Report Template Printable Word Searches
Cyber Security After Action Report Template
Simplify Documentation Of Breaches, Viruses, And Other It Security Events.
How Was The Incident Detected / Discovered?.
Writing An Effective Cybersecurity Incident Report Is A Critical Step In Incident Response.
Instead, Consistent And Transparent Communication Can Mitigate Losses, Preserve Reputation And Maintain Customer Loyalty.
Related Post: