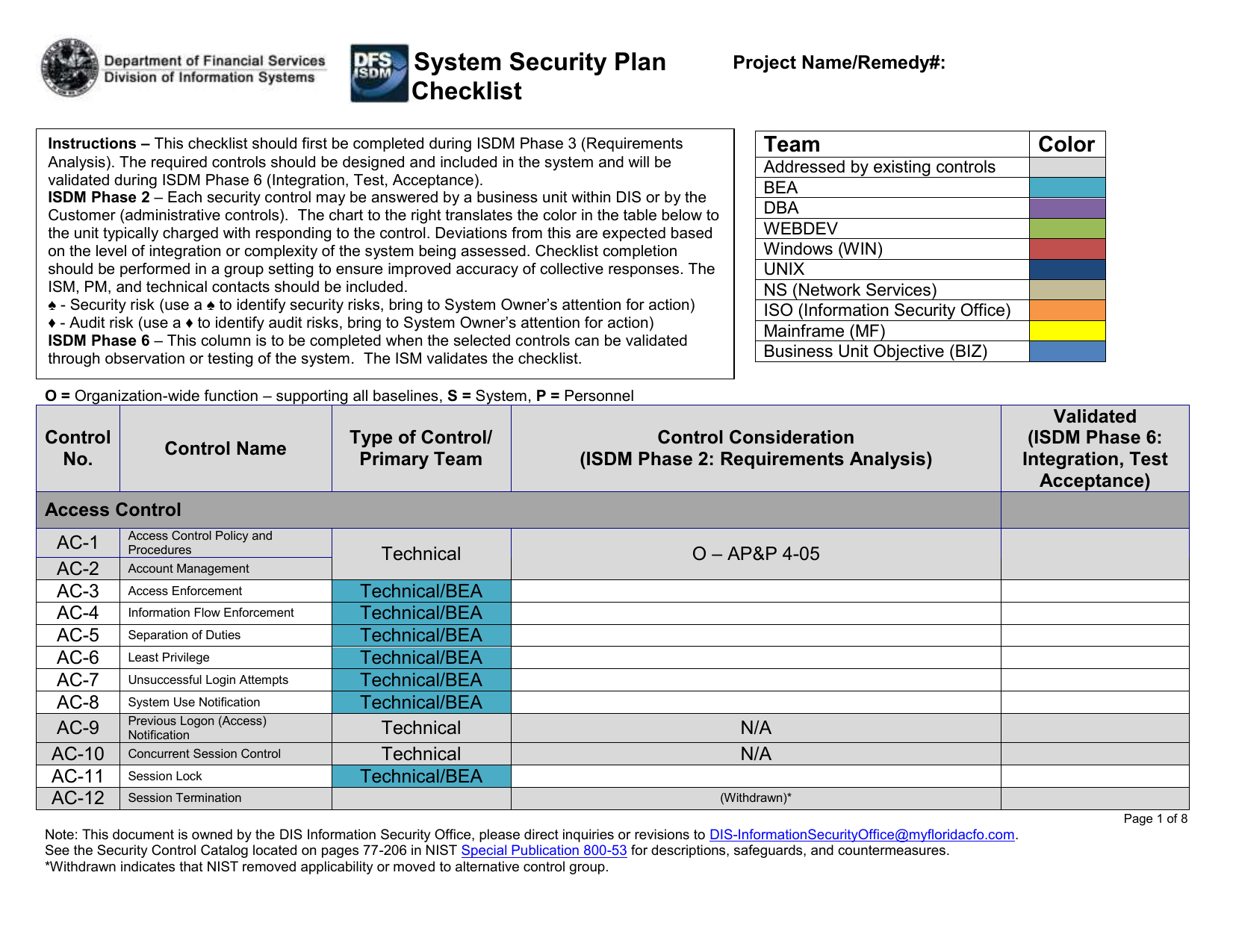
Nist Information Security Policy Template
Nist Information Security Policy Template - Download free policy and standard templates for the nist csf 2.0 identify core function, which focuses on understanding the organizational environment and the risks to its systems, people,. Nist provides a comprehensive information security policy template that can help organizations establish and implement effective security measures to protect their valuable. Sans has developed a set of information security policy templates. Policy template guide nist function: Our list includes policy templates. These are free to use and fully customizable to your company's it security practices. An official website of the united states government. We are seeking your feedback on the publication’s contents and the future direction of nist’s ransomware guidance. It statically audits hcl for security vulnerabilities, including hardcoded credentials, overly permissive iam policies, and improper network settings. By utilizing the nist information security management program template, organizations can establish a robust security program that aligns with industry standards and. View the quick start guides. 16 a cybersecurity framework 2.0 community profile 17 initial public draft 18 murugiah souppaya. The following is a library of free information security policy templates that map to the hitrust common security framework, which in turn maps to a multitude of security frameworks (nist,. Approaches, methodologies, implementation guides, mappings to the framework, case studies, educational materials,. Although not designed to fully meet every compliance requirement, these templates follow the nist cybersecurity framework 2.0 (nsit csf 2.0) core functions of govern,. Resources include, but are not limited to: Our list includes policy templates. Standards a standard is set of prescribed practices or. The collaboration index template supports information security and privacy program collaboration to help ensure that the objectives of both disciplines are met and that. By utilizing the nist information security management program template, organizations can establish a robust security program that aligns with industry standards and. These are free to use and fully customizable to your company's it security practices. By utilizing the nist information security management program template, organizations can establish a robust security program that aligns with industry standards and. 16 a cybersecurity framework 2.0 community profile 17 initial public draft 18 murugiah souppaya. Policy template guide nist function: View the quick start guides. It statically audits hcl for security vulnerabilities, including hardcoded credentials, overly permissive iam policies, and improper network settings. 13 nist internal report 14 nist ir 8374r1 ipd 15 ransomware risk management: This course provides essential guidance to individuals with information security implementation and operational responsibilities for developing and disseminating an. View the quick start guides. We are seeking your feedback. It statically audits hcl for security vulnerabilities, including hardcoded credentials, overly permissive iam policies, and improper network settings. Standards a standard is set of prescribed practices or. For users with specific common goals. By utilizing the nist information security management program template, organizations can establish a robust security program that aligns with industry standards and. 13 nist internal report 14. These are free to use and fully customizable to your company's it security practices. Nist ir 8374 reflects changes made to the. 13 nist internal report 14 nist ir 8374r1 ipd 15 ransomware risk management: We are seeking your feedback on the publication’s contents and the future direction of nist’s ransomware guidance. The collaboration index template supports information security and. Approaches, methodologies, implementation guides, mappings to the framework, case studies, educational materials,. The document outlines the five main functions within the nist csf. It statically audits hcl for security vulnerabilities, including hardcoded credentials, overly permissive iam policies, and improper network settings. By utilizing the nist information security management program template, organizations can establish a robust security program that aligns with. View the quick start guides. 13 nist internal report 14 nist ir 8374r1 ipd 15 ransomware risk management: Nist provides a comprehensive information security policy template that can help organizations establish and implement effective security measures to protect their valuable. These are free to use and fully customizable to your company's it security practices. It statically audits hcl for security. The following is a library of free information security policy templates that map to the hitrust common security framework, which in turn maps to a multitude of security frameworks (nist,. 16 a cybersecurity framework 2.0 community profile 17 initial public draft 18 murugiah souppaya. These are free to use and fully customizable to your company's it security practices. This course. The collaboration index template supports information security and privacy program collaboration to help ensure that the objectives of both disciplines are met and that. These are free to use and fully customizable to your company's it security practices. Approaches, methodologies, implementation guides, mappings to the framework, case studies, educational materials,. An official website of the united states government. Standards a. Standards a standard is set of prescribed practices or. The document outlines the five main functions within the nist csf. The following is a library of free information security policy templates that map to the hitrust common security framework, which in turn maps to a multitude of security frameworks (nist,. Although not designed to fully meet every compliance requirement, these. An official website of the united states government. This course provides essential guidance to individuals with information security implementation and operational responsibilities for developing and disseminating an. For industry, government, and organizations to reduce cybersecurity risks. These are free to use and fully customizable to your company's it security practices. Policy template guide nist function: View the quick start guides. Sans has developed a set of information security policy templates. This course provides essential guidance to individuals with information security implementation and operational responsibilities for developing and disseminating an. 16 a cybersecurity framework 2.0 community profile 17 initial public draft 18 murugiah souppaya. Resources include, but are not limited to: Approaches, methodologies, implementation guides, mappings to the framework, case studies, educational materials,. Standards a standard is set of prescribed practices or. Nist ir 8374 reflects changes made to the. We are seeking your feedback on the publication’s contents and the future direction of nist’s ransomware guidance. 13 nist internal report 14 nist ir 8374r1 ipd 15 ransomware risk management: By utilizing the nist information security management program template, organizations can establish a robust security program that aligns with industry standards and. These are free to use and fully customizable to your company's it security practices. Nist provides a comprehensive information security policy template that can help organizations establish and implement effective security measures to protect their valuable. An official website of the united states government. Although not designed to fully meet every compliance requirement, these templates follow the nist cybersecurity framework 2.0 (nsit csf 2.0) core functions of govern,. Our list includes policy templates.Information Security Policy Templates Nist Template 1 Resume
Policy Template Guide NIST Cybersecurity Framework PDF Security
Nist Information Security Policy Template Master of
Nist Cybersecurity Framework Policy Template Guide
NIST CSF 2.0 Tagged "NIST Information Security Policy Template" IT
Nist Data Protection Policy Template
Nist Information Security Policy Template Master of
Nist Information Security Policy Template Master of
Nist Configuration Management Policy Template
Information Security Roles and Responsibilities Policy and Template
It Statically Audits Hcl For Security Vulnerabilities, Including Hardcoded Credentials, Overly Permissive Iam Policies, And Improper Network Settings.
The Following Is A Library Of Free Information Security Policy Templates That Map To The Hitrust Common Security Framework, Which In Turn Maps To A Multitude Of Security Frameworks (Nist,.
Policy Template Guide Nist Function:
The Document Outlines The Five Main Functions Within The Nist Csf.
Related Post: