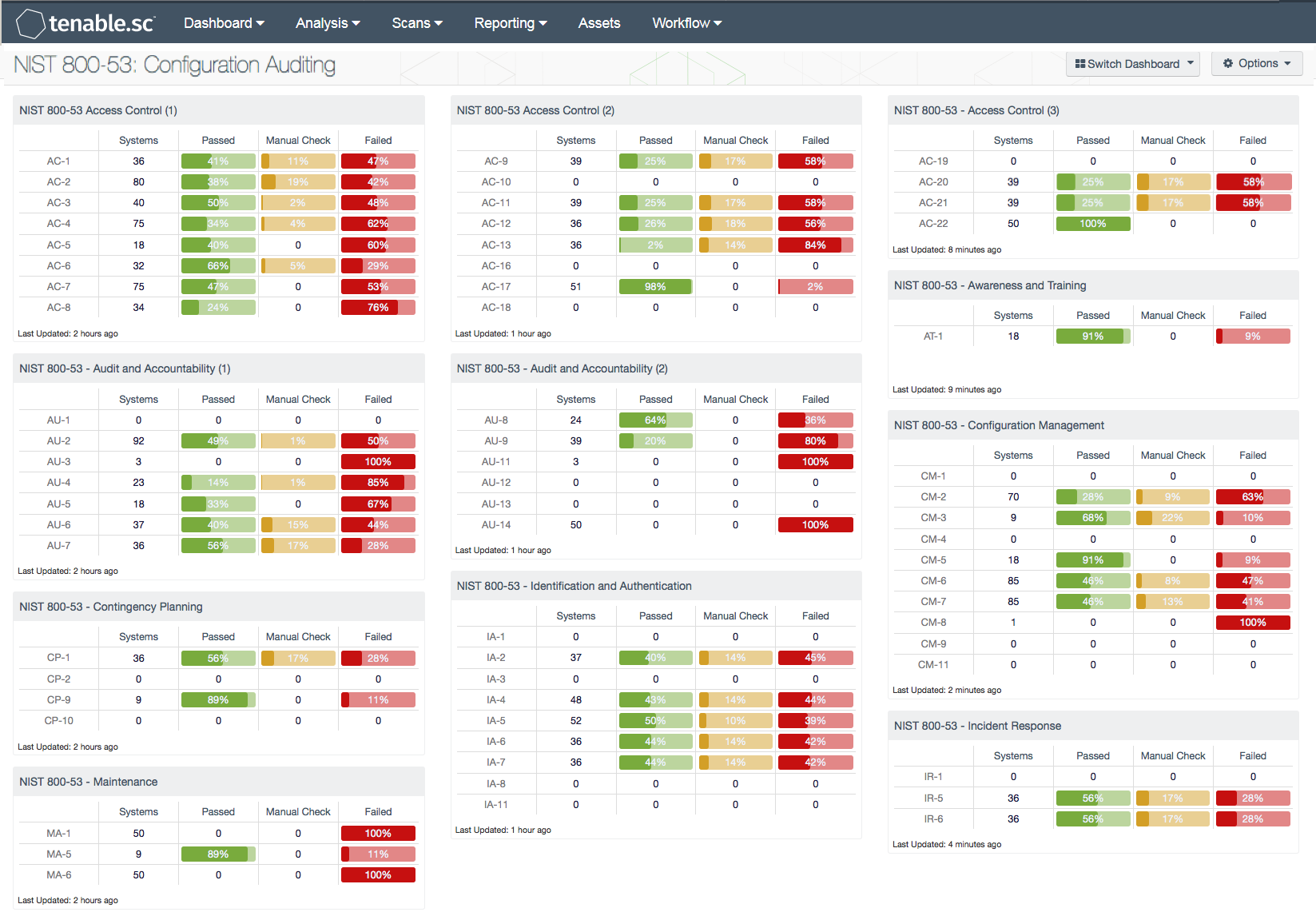
Nist Ssp Template
Nist Ssp Template - Use this downloadable ssp template to develop an ssp for your organization. Learn how to use the oscal system security plan (ssp) model to document the control implementation of an information system. The nist computer security resource center provides resources and templates for developing security plans to protect controlled unclassified information (cui) in nonfederal systems. Aligning your cmmc compliance efforts with your existing controls will help you build a cohesive and streamlined compliance program — and make it easier to create and. This guide provides a framework for developing system security plans for federal information systems. Each section includes a blue box of text like this which describes what the. The ssp model includes metadata, import. It is important to understand that there is no officially‐sanctioned format for a system security plan (ssp) to meet nist 800‐171 compliance requirements. Nist ir 8374 reflects changes made to the cybersecurity framework (csf) from csf 1.1 to csf 2.0 which identifies security objectives that support managing, detecting,. Dod, gsa, and nasa require all contractors and supply chain partners that handle controlled unclassified information (cui) to implement the security safeguards defined. Each section includes a blue box of text like this which describes what the. This template is based on ssp. Learn how to use the oscal system security plan (ssp) model to document the control implementation of an information system. Aligning your cmmc compliance efforts with your existing controls will help you build a cohesive and streamlined compliance program — and make it easier to create and. Use this downloadable ssp template to develop an ssp for your organization. It is important to understand that there is no officially‐sanctioned format for a system security plan (ssp) to meet nist 800‐171 compliance requirements. This guide provides a framework for developing system security plans for federal information systems. Discover key steps and what you should include in your ssp. 2 (02/21/2020) planning note (04/13/2022): Dod, gsa, and nasa require all contractors and supply chain partners that handle controlled unclassified information (cui) to implement the security safeguards defined. Nist ir 8374 reflects changes made to the cybersecurity framework (csf) from csf 1.1 to csf 2.0 which identifies security objectives that support managing, detecting,. The ssp model includes metadata, import. Discover key steps and what you should include in your ssp. It covers the objectives, requirements, structure, and format of security. Aligning your cmmc compliance efforts with your existing. Aligning your cmmc compliance efforts with your existing controls will help you build a cohesive and streamlined compliance program — and make it easier to create and. The nist computer security resource center provides resources and templates for developing security plans to protect controlled unclassified information (cui) in nonfederal systems. It is important to understand that there is no officially‐sanctioned. Based on customer demand, we developed an editable system security plan (ssp) template that is specifically. Aligning your cmmc compliance efforts with your existing controls will help you build a cohesive and streamlined compliance program — and make it easier to create and. This template is based on ssp. Discover key steps and what you should include in your ssp.. It is important to understand that there is no officially‐sanctioned format for a system security plan (ssp) to meet nist 800‐171 compliance requirements. This guide provides a framework for developing system security plans for federal information systems. Learn how to use the oscal system security plan (ssp) model to document the control implementation of an information system. It can be. Aligning your cmmc compliance efforts with your existing controls will help you build a cohesive and streamlined compliance program — and make it easier to create and. Discover key steps and what you should include in your ssp. Dod, gsa, and nasa require all contractors and supply chain partners that handle controlled unclassified information (cui) to implement the security safeguards. It is important to understand that there is no officially‐sanctioned format for a system security plan (ssp) to meet nist 800‐171 compliance requirements. Learn how to use the oscal system security plan (ssp) model to document the control implementation of an information system. It covers the objectives, requirements, structure, and format of security. Discover key steps and what you should. It is important to understand that there is no officially‐sanctioned format for a system security plan (ssp) to meet nist 800‐171 compliance requirements. 2 (02/21/2020) planning note (04/13/2022): Learn how to use the oscal system security plan (ssp) model to document the control implementation of an information system. Aligning your cmmc compliance efforts with your existing controls will help you. This template is based on ssp. Discover key steps and what you should include in your ssp. The ssp model includes metadata, import. Based on customer demand, we developed an editable system security plan (ssp) template that is specifically. The nist computer security resource center provides resources and templates for developing security plans to protect controlled unclassified information (cui) in. It covers the objectives, requirements, structure, and format of security. Based on customer demand, we developed an editable system security plan (ssp) template that is specifically. Each section includes a blue box of text like this which describes what the. This guide provides a framework for developing system security plans for federal information systems. Aligning your cmmc compliance efforts with. Learn how to use the oscal system security plan (ssp) model to document the control implementation of an information system. It covers the objectives, requirements, structure, and format of security. Each section includes a blue box of text like this which describes what the. The ssp model includes metadata, import. Based on customer demand, we developed an editable system security. This template is based on ssp. Based on customer demand, we developed an editable system security plan (ssp) template that is specifically. It is important to understand that there is no officially‐sanctioned format for a system security plan (ssp) to meet nist 800‐171 compliance requirements. It covers the objectives, requirements, structure, and format of security. Each section includes a blue box of text like this which describes what the. This guide provides a framework for developing system security plans for federal information systems. 2 (02/21/2020) planning note (04/13/2022): The ssp model includes metadata, import. It can be used for both public and private sector systems and. Use this downloadable ssp template to develop an ssp for your organization. Discover key steps and what you should include in your ssp. Aligning your cmmc compliance efforts with your existing controls will help you build a cohesive and streamlined compliance program — and make it easier to create and.Nist 800 171 Ssp Template
NIST 800171 System Security Plan (SSP) Template
Nist Sp 800171 Ssp Template
Nist System Security Plan Template Master of Documents
TEMPLATE The NIST 800171 System Security Plan (SSP) ⋆ The Cyber Sentinel
System Security Plan Ssp Template Workbook Nist Based A Doc
System Security Plan Template Nist 800171
Nist 800 53 Ssp Template
Nist 800 53 Ssp Template
NIST 80053, Revision 5 System Security Plan (SSP) Template HIGH
Nist Ir 8374 Reflects Changes Made To The Cybersecurity Framework (Csf) From Csf 1.1 To Csf 2.0 Which Identifies Security Objectives That Support Managing, Detecting,.
Dod, Gsa, And Nasa Require All Contractors And Supply Chain Partners That Handle Controlled Unclassified Information (Cui) To Implement The Security Safeguards Defined.
The Nist Computer Security Resource Center Provides Resources And Templates For Developing Security Plans To Protect Controlled Unclassified Information (Cui) In Nonfederal Systems.
Learn How To Use The Oscal System Security Plan (Ssp) Model To Document The Control Implementation Of An Information System.
Related Post: