Pii Policy Template
Pii Policy Template - Sample breach of personally identifiable information (pii) policy. Itl develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. Omb defines “personally identifiable information” (pii) as information that can be used to distinguish or trace an individual’s identity, either alone or when combined with other. Key features of the template and guidance adaptable provisions with contextual guidance: Unique information that can be used on its own or in combinations with other information to identify an individual. Learn what pii is, why you need a pii policy, and how to create one. This personally identifiable information (pii) protection at workstations policy covers the responsibilities of personnel regarding the protection of information assets when unattended in. It covers the definition, types, examples, and. The document not only provides policy provisions but also offers context for each. These are free to use and fully customizable to your company's it security practices. A personally identifiable information policy template is a comprehensive framework that outlines the procedures and policies for handling and safeguarding personal information. This document provides guidance for federal agencies on protecting the confidentiality of personally identifiable information (pii) in information systems. The following template has been created by the massachusetts office for victim assistance (mova). It covers the definition, types, examples, and. Personally identifiable information (pii) defined as information about a person that contains some unique identifier, including but not limited to name or social security number, from which the. This handbook provides best practices and dhs policy requirements to prevent a privacy incident involving pii/spii during all stages of the information lifecycle: Sans has developed a set of information security policy templates. Unique information that can be used on its own or in combinations with other information to identify an individual. Learn what pii is, why you need a pii policy, and how to create one. This handbook provides best practices and dhs policy requirements to prevent a privacy incident involving pii/spii during all stages of the information lifecycle: Sample breach of personally identifiable information (pii) policy. “pii that when lost, compromised or disclosed. This document provides guidance for federal agencies on protecting the confidentiality of personally identifiable information (pii) in information systems. The document not only provides policy provisions but also offers context for each. This handbook provides best practices and dhs policy requirements to prevent a privacy. The document not only provides policy provisions but also offers context for each. Pii may reside in hard copy or. Learn what pii is, why you need a pii policy, and how to create one. Sample breach of personally identifiable information (pii) policy. The following template has been created by the massachusetts office for victim assistance (mova). The following template has been created by the massachusetts office for victim assistance (mova). Pii may reside in hard copy or. Sans has developed a set of information security policy templates. This directive provides gsa’s policy on how to properly handle pii and the. It outlines the procedures for. This handbook provides best practices and dhs policy requirements to prevent a privacy incident involving pii/spii during all stages of the information lifecycle: Key features of the template and guidance adaptable provisions with contextual guidance: It covers the definition, types, examples, and. It outlines the procedures for. Personally identifiable information (pii) is described as any electronic data that can be. This personally identifiable information (pii) protection at workstations policy covers the responsibilities of personnel regarding the protection of information assets when unattended in. This handbook provides best practices and dhs policy requirements to prevent a privacy incident involving pii/spii during all stages of the information lifecycle: Itl develops tests, test methods, reference data, proof of concept implementations, and technical analysis. Pii is sometimes also called “personally identifiable information,” “personal protected information” or ppi, and other similar terms and acronyms. The document not only provides policy provisions but also offers context for each. Key features of the template and guidance adaptable provisions with contextual guidance: This handbook provides best practices and dhs policy requirements to prevent a privacy incident involving pii/spii. Personally identifiable information (pii) is described as any electronic data that can be used to disclose the identity of an individual. Sans has developed a set of information security policy templates. This personally identifiable information (pii) protection at workstations policy covers the responsibilities of personnel regarding the protection of information assets when unattended in. This document provides guidance for federal. Our list includes policy templates. The document not only provides policy provisions but also offers context for each. “pii that when lost, compromised or disclosed. Personally identifiable information (pii) defined as information about a person that contains some unique identifier, including but not limited to name or social security number, from which the. These are free to use and fully. It outlines the procedures for. Sample breach of personally identifiable information (pii) policy. This personally identifiable information (pii) protection at workstations policy covers the responsibilities of personnel regarding the protection of information assets when unattended in. Personally identifiable information (pii) is described as any electronic data that can be used to disclose the identity of an individual. It covers the. Personally identifiable information (pii) defined as information about a person that contains some unique identifier, including but not limited to name or social security number, from which the. The following template has been created by the massachusetts office for victim assistance (mova). This document provides guidance for federal agencies on protecting the confidentiality of personally identifiable information (pii) in information. This directive provides gsa’s policy on how to properly handle pii and the. Personally identifiable information (pii) defined as information about a person that contains some unique identifier, including but not limited to name or social security number, from which the. This handbook provides best practices and dhs policy requirements to prevent a privacy incident involving pii/spii during all stages of the information lifecycle: This document provides guidance for federal agencies on protecting the confidentiality of personally identifiable information (pii) in information systems. A personally identifiable information policy template is a comprehensive framework that outlines the procedures and policies for handling and safeguarding personal information. These are free to use and fully customizable to your company's it security practices. Pii may reside in hard copy or. Gsa rules of behavior for handling personally identifiable information (pii) purpose: This handbook provides best practices and dhs policy requirements to prevent a privacy incident involving pii/spii during all stages of the information lifecycle: Learn what pii is, why you need a pii policy, and how to create one. Pii is sometimes also called “personally identifiable information,” “personal protected information” or ppi, and other similar terms and acronyms. Personally identifiable information (pii) is described as any electronic data that can be used to disclose the identity of an individual. This article covers the basics of pii, data mapping, states of data, and regulations that cover pi… Key features of the template and guidance adaptable provisions with contextual guidance: The document not only provides policy provisions but also offers context for each. The following template has been created by the massachusetts office for victim assistance (mova).Pii Policy Template
Pii Policy Template
Free PII Compliance Checklist Template Edit Online & Download
Pii Policy Template
Identifying And Safeguarding Pii V4 Test Out Answers Identif
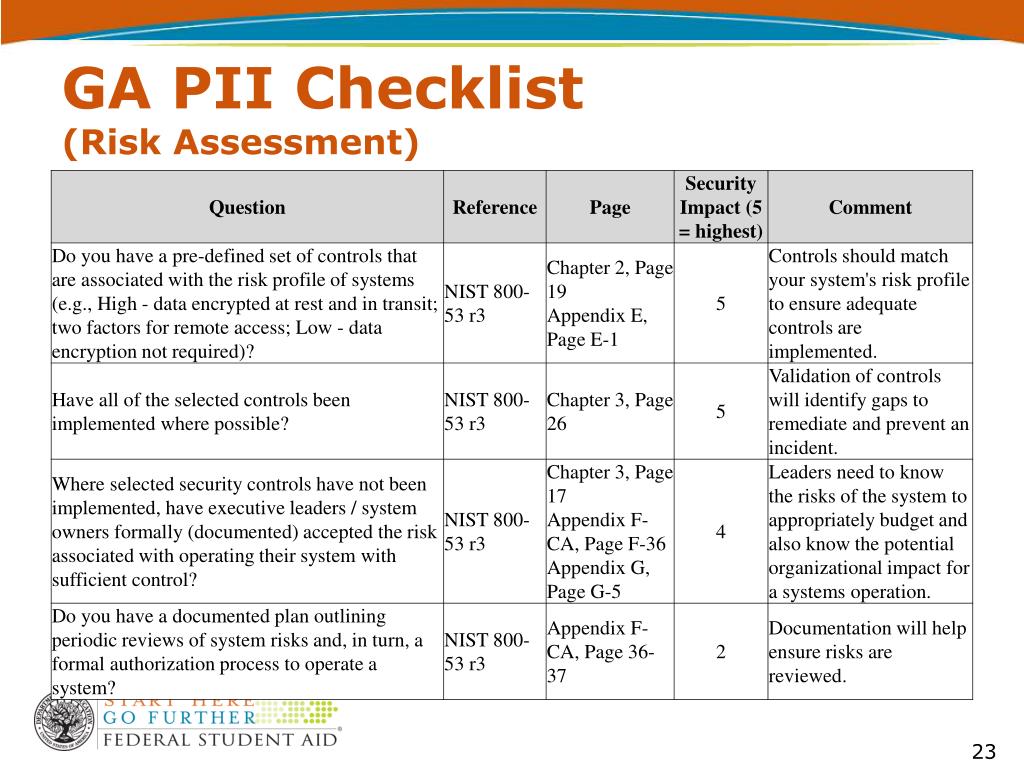
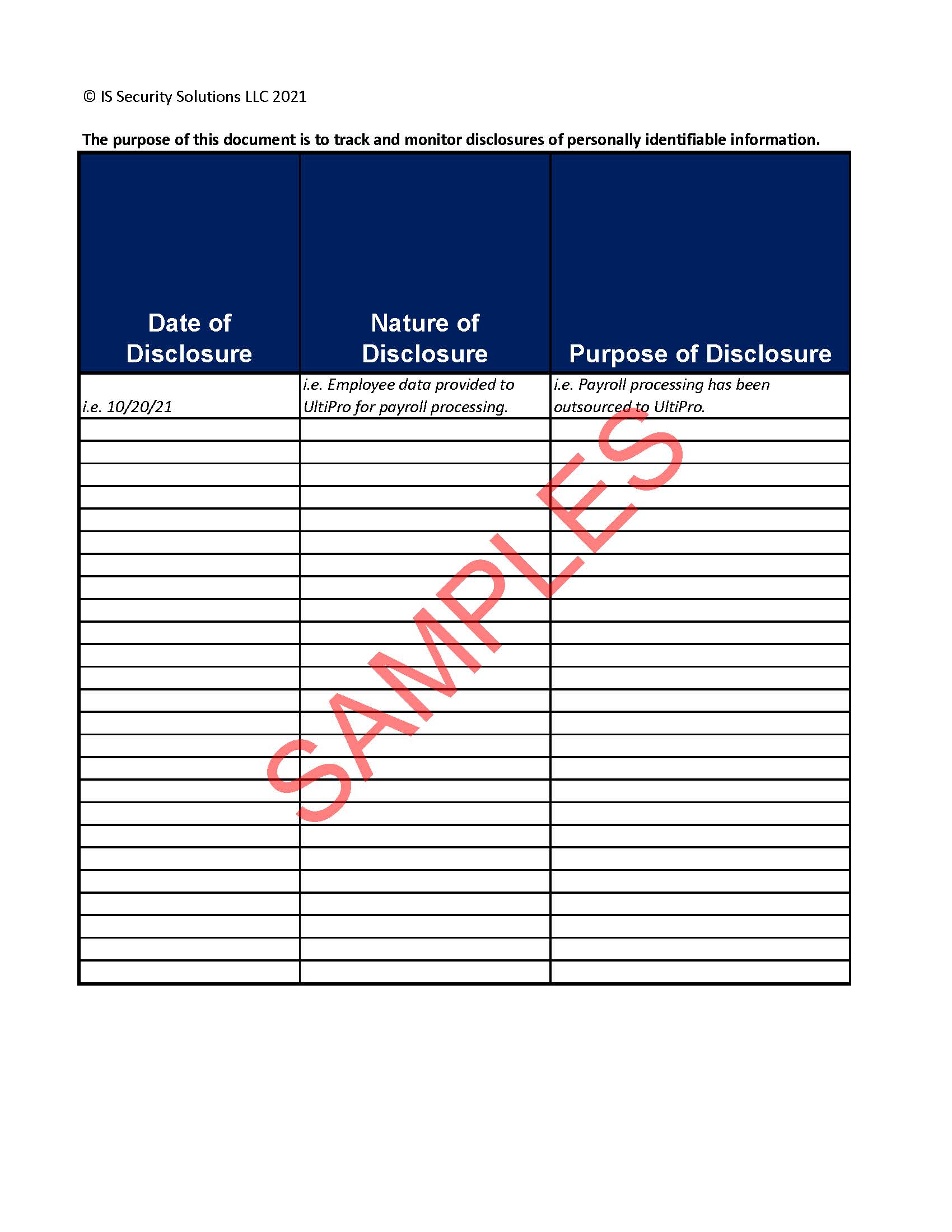
Accounting of Personally Identifiable Information Disclosures Template
Pii Policy Template
PrivacyandPersonalInformationPolicy
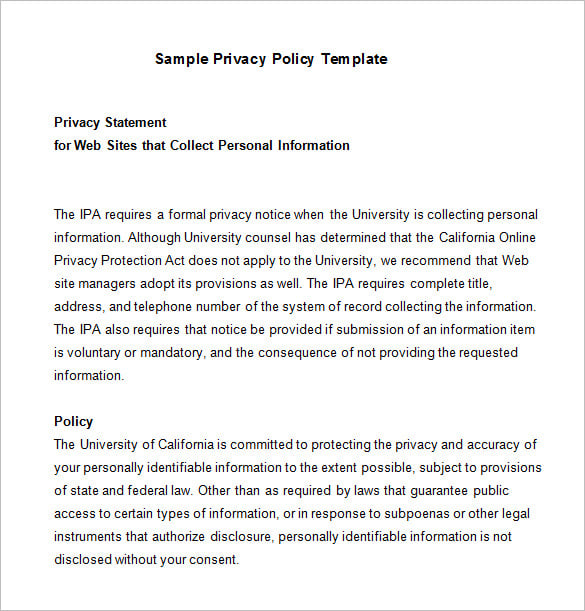
Sample Data Protection Policy Template Information Privacy
ITDonut Sample DP Policy Template Information Privacy Personally
Unique Information That Can Be Used On Its Own Or In Combinations With Other Information To Identify An Individual.
“Pii That When Lost, Compromised Or Disclosed.
Itl Develops Tests, Test Methods, Reference Data, Proof Of Concept Implementations, And Technical Analysis To Advance The Development And Productive Use Of Information Technology.
Our List Includes Policy Templates.
Related Post: