Ransomware Playbook Template
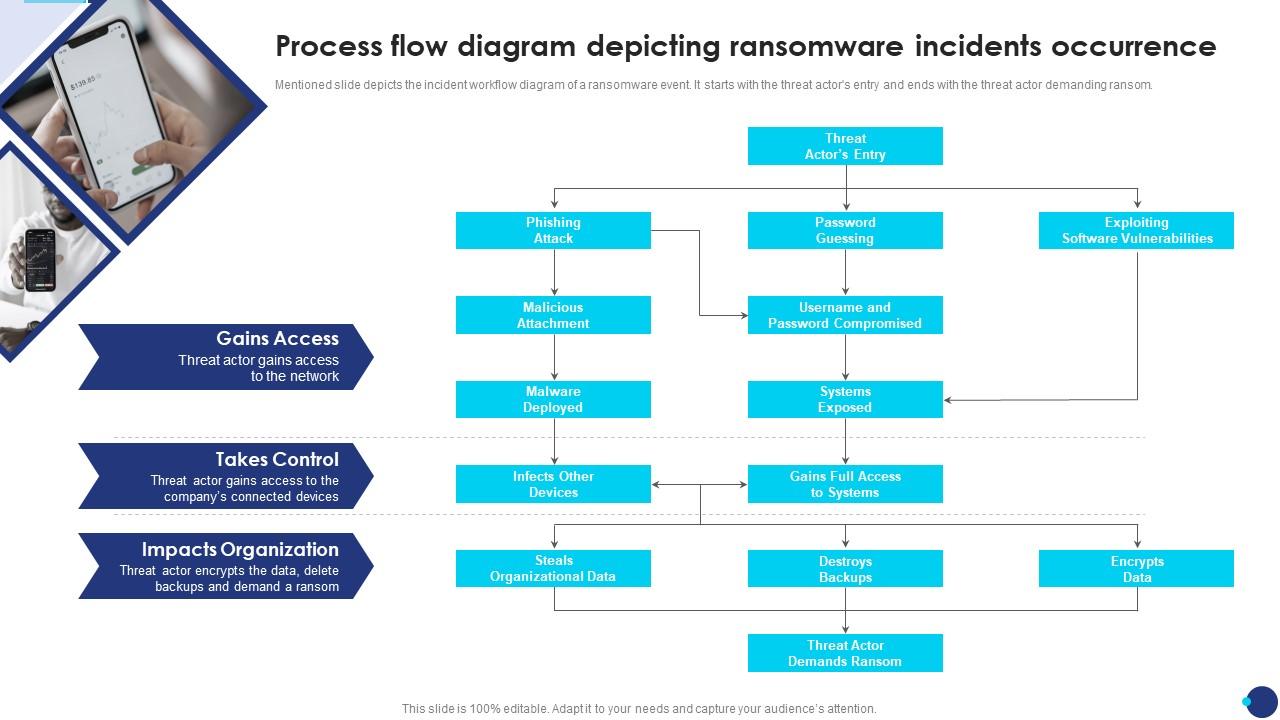
Ransomware Playbook Template - This playbook outlines response steps for handling ransomware incidents. The playbook defines key stakeholders,. These new emulations are intended to expand fin7’s playbook by incorporating tactics, techniques, and procedures (ttps) exhibited during its historical activities. Iain mulholland, senior director, security engineering, shares insights on the state of ransomware. Ransomware response playbook knowing exactly what to do when a cyberattack happens makes all the difference between a small incident and a costly breach. Welcome to the second cloud ciso perspectives for january 2025. This document is a generic playbook based on the government of alberta’s ransomware standard operating procedure. Ransomware can attack organizations of all sizes from any sector. The playbook defines key stakeholders,. You can use this document to construct your own organization’s. You can use this publication to gauge your organization’s readiness to counter ransomware threats,. This playbook will outline indicators of compromise (ioc) that will be used to identify infected machines or malicious activity, as well as response actions to take to mitigate the impact of a. We’ve released a detailed, customizable playbook for ransomware to enhance your incident response plan and reduce the impact of ransomware incidents. The playbook defines key stakeholders,. It then provides a framework for the. This comprehensive ransomware incident playbook guide shows you how to create an effective incident playbook to respond effectively to ransomware attacks. You can use this document to construct your own organization’s. Building an effective incident response playbook. An organization should focus on. Welcome to the second cloud ciso perspectives for january 2025. Data loss prevention, intrusion prevention, cloud malware detection, remote b. The playbook defines key stakeholders, processes, policies & prevention plans to defend your organization. An organization should focus on. This comprehensive ransomware incident playbook guide shows you how to create an effective incident playbook to respond effectively to ransomware attacks. It then provides a framework for the. This ransomware playbook is intended to be used as a general guideline for organizations faced with ransomware attacks. This document is a generic playbook based on the government of alberta’s ransomware standard operating procedure. It then provides a framework for the. It discusses what a ransomware ir playbook is, why it is needed, who should be involved in developing it,. It includes detailed guidelines on forming a cybersecurity. An organization should focus on. Detect, respond, and recover from ransomware incidents. A concise and customizable template designed for organizations to develop their own ransomware response playbook. This ransomware playbook is intended to be used as a general guideline for organizations faced with ransomware attacks. If you are currently experiencing a ransomware incident, it is highly. Collects logs and rapid threat detection. The playbook defines key stakeholders,. Data loss prevention, intrusion prevention, cloud malware detection, remote b. Building an effective incident response playbook. This ransomware playbook is intended to be used as a general guideline for organizations faced with ransomware attacks. On firewall secure dns/ip layer security. These new emulations are intended to expand fin7’s playbook by incorporating tactics, techniques, and procedures (ttps) exhibited during its historical activities. A concise and customizable template designed for organizations to develop their own ransomware response playbook.. This ransomware playbook is intended to be used as a general guideline for organizations faced with ransomware attacks. Detect, respond, and recover from ransomware incidents. This comprehensive ransomware incident playbook guide shows you how to create an effective incident playbook to respond effectively to ransomware attacks. This document is a generic playbook based on the government of alberta’s ransomware standard. On firewall secure dns/ip layer security. It then provides a framework for the. These new emulations are intended to expand fin7’s playbook by incorporating tactics, techniques, and procedures (ttps) exhibited during its historical activities. If you are currently experiencing a ransomware incident, it is highly. The playbook defines key stakeholders,. You can use this document to construct your own organization’s. Building an effective incident response playbook. On firewall secure dns/ip layer security. Creating an effective incident response playbook requires a strategic approach to ensure preparedness for any cybersecurity incident:. Data loss prevention, intrusion prevention, cloud malware detection, remote b. The playbook defines key stakeholders, processes, policies & prevention plans to defend your organization. These new emulations are intended to expand fin7’s playbook by incorporating tactics, techniques, and procedures (ttps) exhibited during its historical activities. This comprehensive ransomware incident playbook guide shows you how to create an effective incident playbook to respond effectively to ransomware attacks. This playbook outlines response. Ransomware is a unique security threat where most of the security team’s efort is spent on prevention and response because once ransomware is detected, it’s too late. A ransomware attack by taking preventative actions (e.g., creating a backup of critical data) and developing and testing a ransomware incident response plan. This comprehensive ransomware incident playbook guide shows you how to. You can use this document to construct your own organization’s. Ransomware response playbook knowing exactly what to do when a cyberattack happens makes all the difference between a small incident and a costly breach. Many organizations simply don’t know how to protect against ransomware. Ransomware can attack organizations of all sizes from any sector. The playbook defines key stakeholders, processes, policies & prevention plans to defend your organization. Collects logs and rapid threat detection. You can use this publication to gauge your organization’s readiness to counter ransomware threats,. Ransomware is a unique security threat where most of the security team’s efort is spent on prevention and response because once ransomware is detected, it’s too late. It then provides a framework for the. The playbook defines key stakeholders,. Building an effective incident response playbook. On firewall secure dns/ip layer security. A ransomware attack by taking preventative actions (e.g., creating a backup of critical data) and developing and testing a ransomware incident response plan. These new emulations are intended to expand fin7’s playbook by incorporating tactics, techniques, and procedures (ttps) exhibited during its historical activities. Data loss prevention, intrusion prevention, cloud malware detection, remote b. A concise and customizable template designed for organizations to develop their own ransomware response playbook.Quick Facts from the Ransomware Playbook Cyber Readiness Institute
Ransomware Response Playbook Policy Template Banking and Fintech
Ransomware Playbook Template
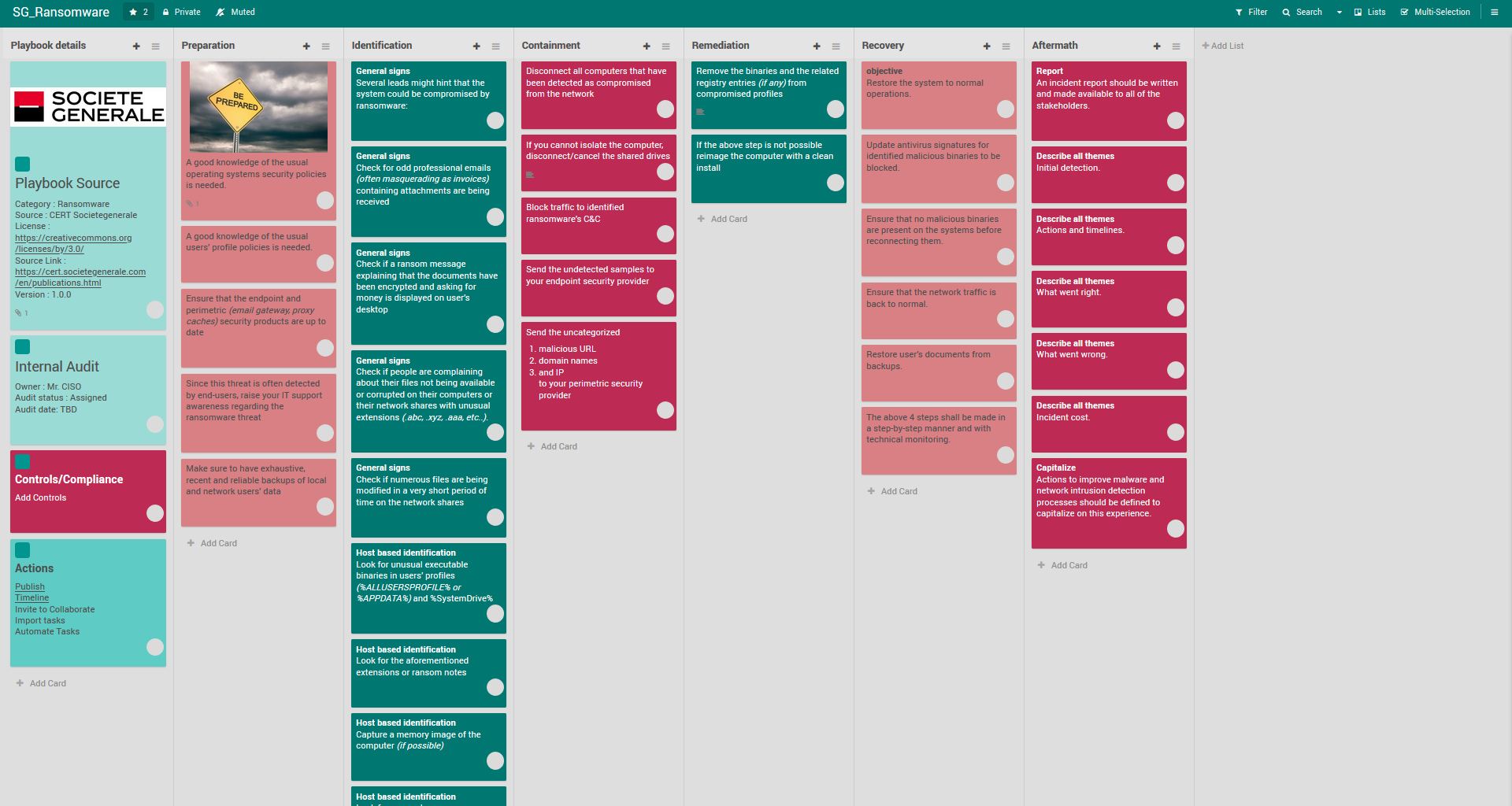
Ransomware Incident Response Playbook Template Ransomware incident
Ransomware Playbook Template
Ransomware Playbook Template
Ransomware Playbook Template
Free Ransomware Incident Response Playbook Protect Your Organization Now
Top 10 Ransomware Playbooks PowerPoint Presentation Templates in 2024
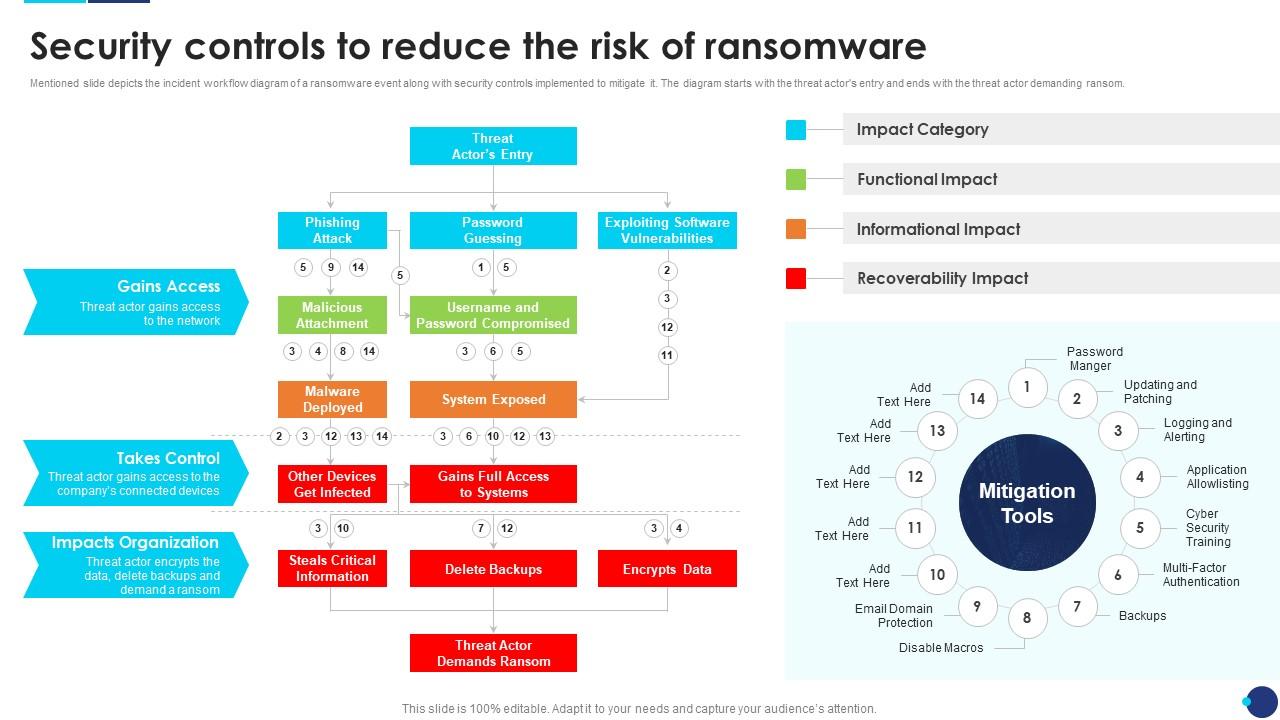
Incident Response Playbook Security Controls To Reduce The Risk Of
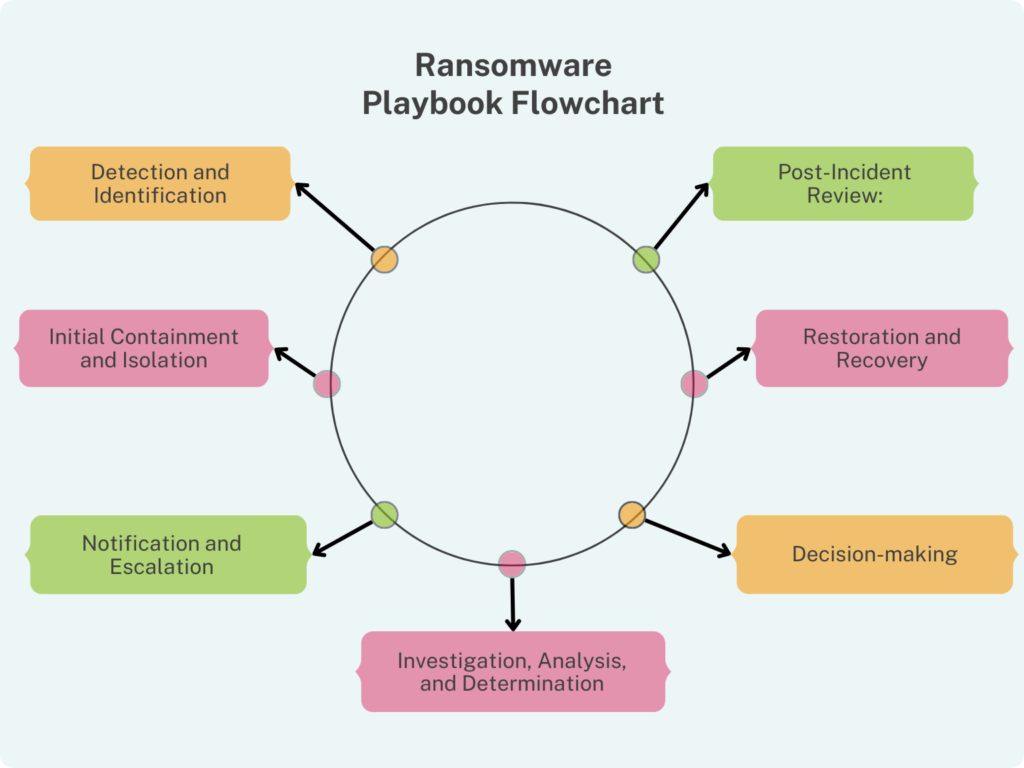
This Playbook Outlines Response Steps For Handling Ransomware Incidents.
If You Are Currently Experiencing A Ransomware Incident, It Is Highly.
An Organization Should Focus On.
Creating An Effective Incident Response Playbook Requires A Strategic Approach To Ensure Preparedness For Any Cybersecurity Incident:.
Related Post: