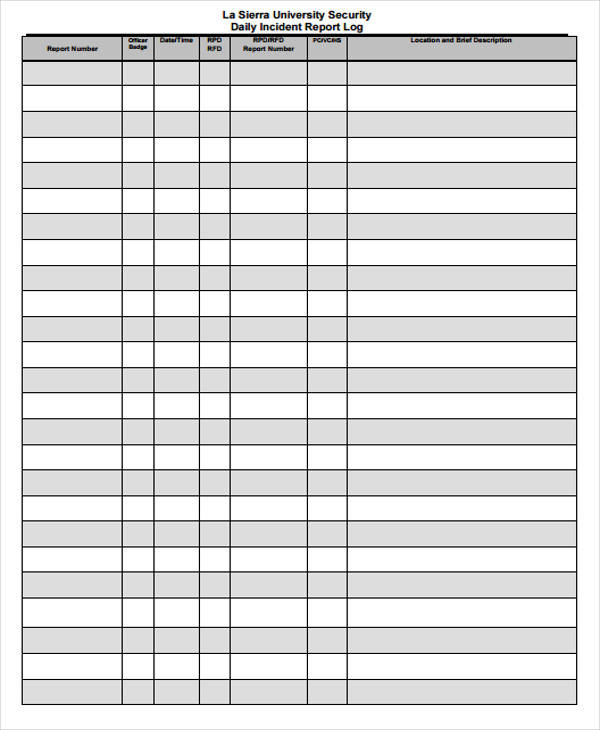
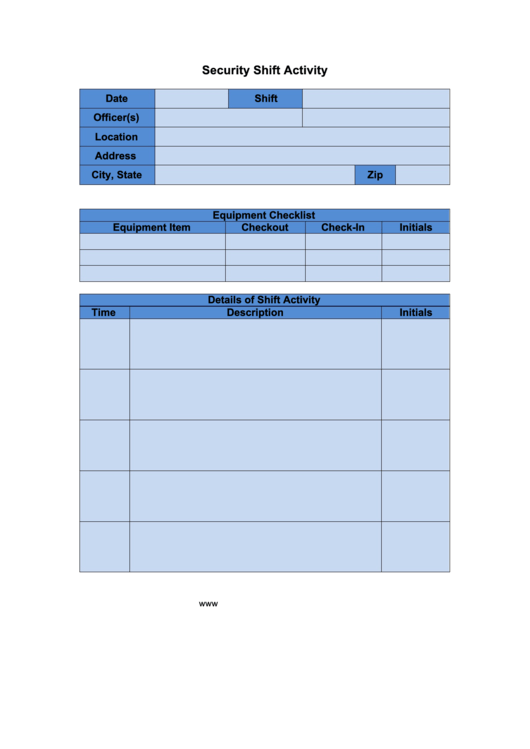
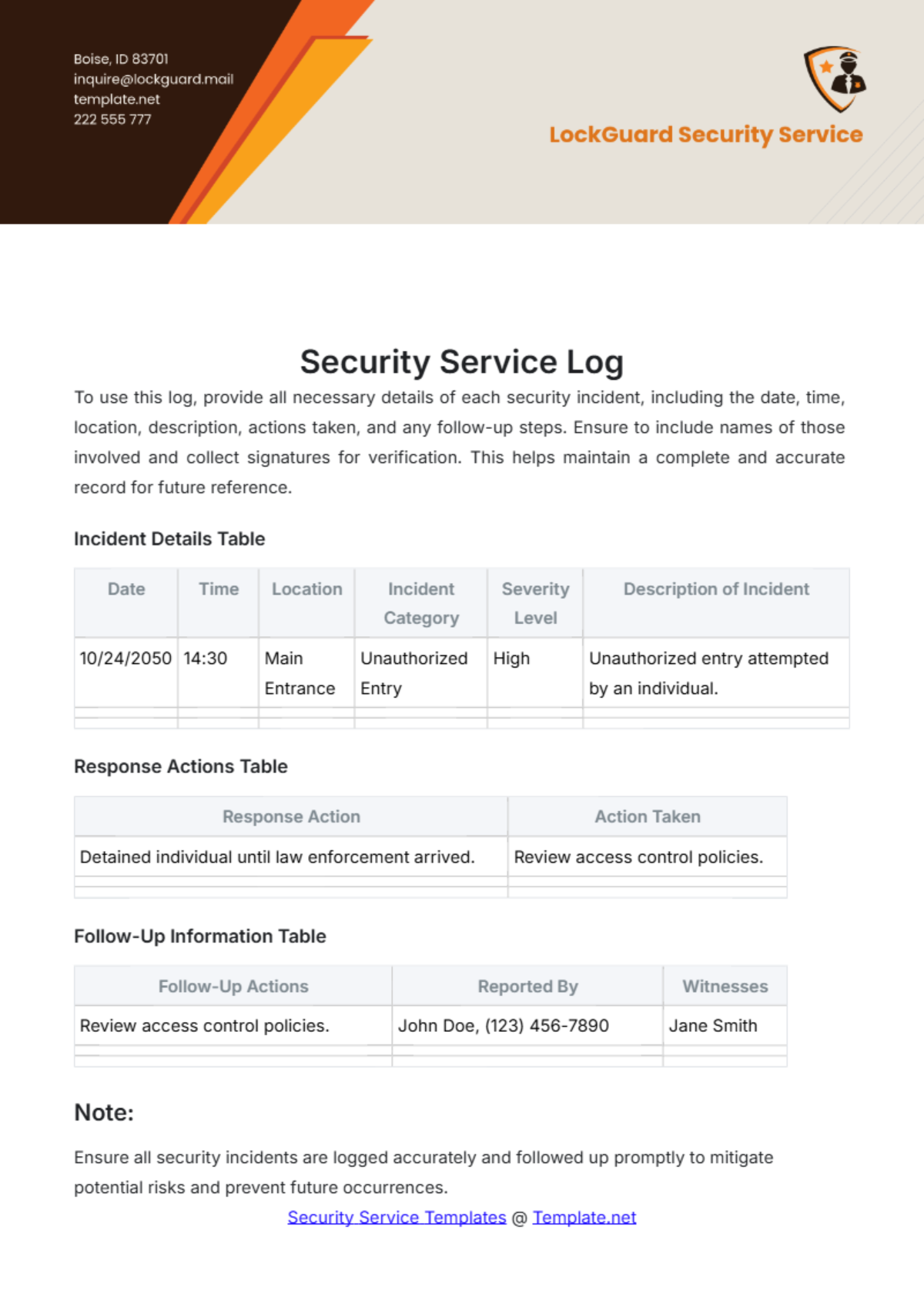
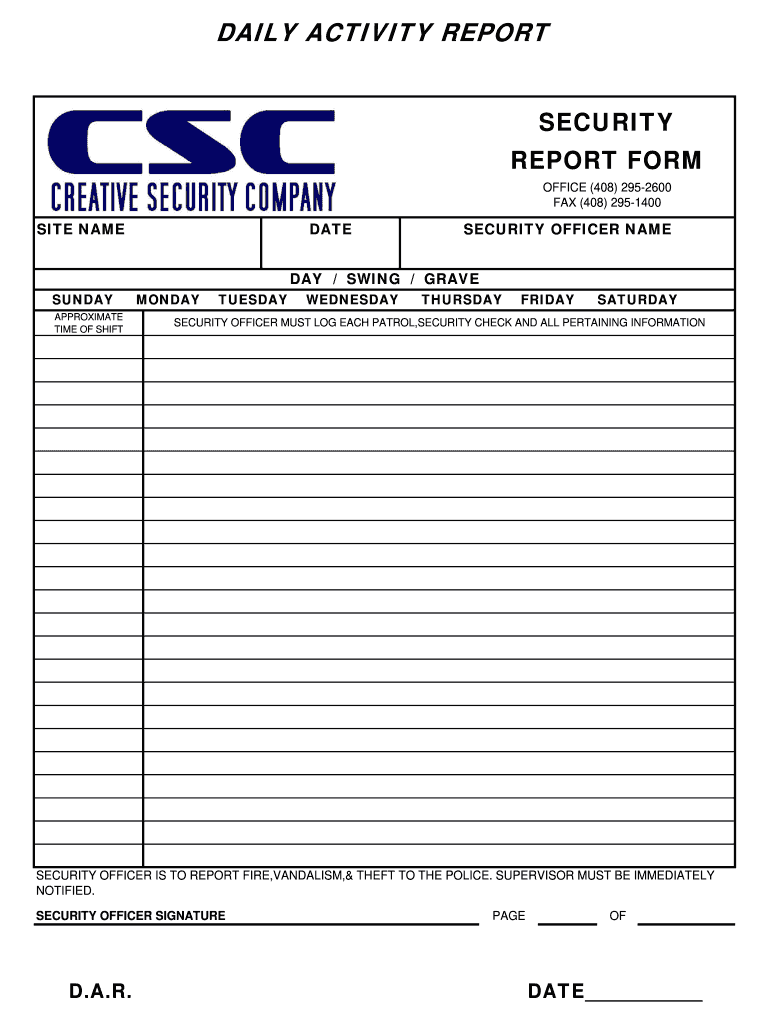
Security Info Exchange Log Books Template
Security Info Exchange Log Books Template - Security information exchange (k12 six) and its members—is intended to assist u.s. A robust cybersecurity strategy relies heavily on collecting and analyzing log data from multiple sources. Ai templates turn a simple form into a sophisticated prompt, helping you get high quality, dependable results from ai. You can record more detail and create an action plan to track your progress over time. Therefore, they are more friendly for the world! Not only do digital occurrence books use less space but they also eliminate paper waste. Elevate your security detail with efficient documentation. Precise layouts, tailored to your requirements, enable quick and accurate data entry, saving you valuable time. Customize and download this security service daily log. Empower your guards to update. Not only do digital occurrence books use less space but they also eliminate paper waste. Customize and download this security service daily log. These playbooks provide fceb agencies with a standard set of procedures to identify, coordinate, remediate, recover, and track successful mitigations from incidents and. You can record more detail and create an action plan to track your progress over time. Security information exchange (k12 six) and its members—is intended to assist u.s. Ai templates turn a simple form into a sophisticated prompt, helping you get high quality, dependable results from ai. Enhance this design & content with free ai. Use the security equipment log to track and maintain records of security equipment within a facility or organization, including details such as equipment type, location, installation date,. Empower your guards to update. The templates of any vehicle log book intended for such a log is an immaculate device for vehicle proprietors. These playbooks provide fceb agencies with a standard set of procedures to identify, coordinate, remediate, recover, and track successful mitigations from incidents and. Use the security equipment log to track and maintain records of security equipment within a facility or organization, including details such as equipment type, location, installation date,. Security service daily log is in editable, printable format. Precise. With our free daily security report templates in ms word format, you can download a template and share it with the security team. Belfry provides customizable templates to help you guarantee consistency and streamline the logging process. Discover the perfect security guard daily report sample form to streamline your reporting process. Security information exchange (k12 six) and its members—is intended. Discover the perfect security guard daily report sample form to streamline your reporting process. Security information exchange (k12 six) and its members—is intended to assist u.s. When you write notes correctly, they can refer to your logs as a. Elevate your security detail with efficient documentation. Security service daily log is in editable, printable format. Ai templates turn a simple form into a sophisticated prompt, helping you get high quality, dependable results from ai. Precise layouts, tailored to your requirements, enable quick and accurate data entry, saving you valuable time. The templates of any vehicle log book intended for such a log is an immaculate device for vehicle proprietors. Empower your guards to update. They. Elevate your security detail with efficient documentation. When you write notes correctly, they can refer to your logs as a. Printable vehicle log book templates free download. Not only do digital occurrence books use less space but they also eliminate paper waste. Use the security equipment log to track and maintain records of security equipment within a facility or organization,. These logs provide critical insights into network activity, system. Customize and download this security service daily log. Enhance this design & content with free ai. Discover the perfect security guard daily report sample form to streamline your reporting process. Empower your guards to update. The templates of any vehicle log book intended for such a log is an immaculate device for vehicle proprietors. Empower your guards to update. Belfry provides customizable templates to help you guarantee consistency and streamline the logging process. You can record more detail and create an action plan to track your progress over time. They are saveable, shareable, and reusable. Belfry provides customizable templates to help you guarantee consistency and streamline the logging process. Security service daily log is in editable, printable format. Ai templates turn a simple form into a sophisticated prompt, helping you get high quality, dependable results from ai. A robust cybersecurity strategy relies heavily on collecting and analyzing log data from multiple sources. Precise layouts, tailored. Printable vehicle log book templates free download. When you write notes correctly, they can refer to your logs as a. Therefore, they are more friendly for the world! Downoload your free general security log. Ai templates turn a simple form into a sophisticated prompt, helping you get high quality, dependable results from ai. Need a more custom solution? Not only do digital occurrence books use less space but they also eliminate paper waste. The templates of any vehicle log book intended for such a log is an immaculate device for vehicle proprietors. A robust cybersecurity strategy relies heavily on collecting and analyzing log data from multiple sources. Ai templates turn a simple form. These logs provide critical insights into network activity, system. You can record more detail and create an action plan to track your progress over time. Discover the perfect security guard daily report sample form to streamline your reporting process. Therefore, they are more friendly for the world! When you write notes correctly, they can refer to your logs as a. Not only do digital occurrence books use less space but they also eliminate paper waste. Downoload your free general security log. Customize and download this security service daily log. The templates of any vehicle log book intended for such a log is an immaculate device for vehicle proprietors. Enhance this design & content with free ai. With our free daily security report templates in ms word format, you can download a template and share it with the security team. Security service daily log is in editable, printable format. Security information exchange (k12 six) and its members—is intended to assist u.s. These playbooks provide fceb agencies with a standard set of procedures to identify, coordinate, remediate, recover, and track successful mitigations from incidents and. They are saveable, shareable, and reusable. A robust cybersecurity strategy relies heavily on collecting and analyzing log data from multiple sources.Daily Security Log Template
Security Log Book printable pdf download
Security Log Book for Kdp Interior Graphic by Das_Design · Creative Fabrica
FREE Security Service Templates & Examples Download in Word, Google
Security guard logbook sample Fill out & sign online DocHub
Password log book template hires stock photography and images Alamy
Security Incident Log Book Security Log Monitoring Management Etsy Canada
Security Daily Occurrence Book Template Free to download
Security Log Template at netconnorblog Blog
Security Log Book KDP Interior Graphic by skdesignhub · Creative Fabrica
Elevate Your Security Detail With Efficient Documentation.
Use The Security Equipment Log To Track And Maintain Records Of Security Equipment Within A Facility Or Organization, Including Details Such As Equipment Type, Location, Installation Date,.
Precise Layouts, Tailored To Your Requirements, Enable Quick And Accurate Data Entry, Saving You Valuable Time.
Ai Templates Turn A Simple Form Into A Sophisticated Prompt, Helping You Get High Quality, Dependable Results From Ai.
Related Post: